
Unused apps, error logs, and user bloat are some things that may be cluttering up your computer, causing it to…

Hackers are known by the general public as cybercriminals, especially with so much news about nude celebrity photos beings released…
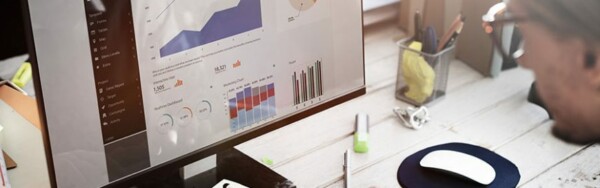
Microsoft’s Workplace Analytics uses data gathered from email, documents, calendar, and other Office 365 applications to present a clear picture…

Most small- to medium-sized businesses (SMBs) don’t possess the resources to run and maintain their IT infrastructure, let alone assess…

Bloatware is software that nobody asked for but is on your computer, taking up valuable space. These software apps come…

Cybersecurity is a threat to businesses across industries. Sometimes, organizations invest in security software without realizing the risks that come…

With Microsoft Excel’s new features being so incredibly user-friendly, there’s no excuse to remain basic. Upgrade your skills with our…

Virtual reality (VR), the technology that immerses users in digitally created simulated experiences, is experiencing a surge in growth. There…

Windows 10 users receive regular security and feature updates for the operating system. But when such patches coincide with driver…